

ROOTT
was established by over 15 years professional expertise team in information systems security and penetration testing We conducted penetration test for many large banks, large TELCOs and large state-own enterprises, please feel free to contact us as information below


External Threat
• Overall internet threats
• Public-facing servers
• Public web sites
• Internet applications
Insider Threat
• Insider threats
• Business logic flaws
• Internal security policy flaws
• Test security awareness of users
• Internal applications
Safeguard Effective
• Existing security controls e.g. firewall, IPS effectiveness
• Security misconfiguration
Before Publish
• Source code security
• Test before publish on UAT and/or production servers
• Business logic flaws
• Security policy flaws
Methodology and approach
Web Application Penetration Test
The primary purpose of this testing is to identify and exploit application and/or code vulnerabilities to demonstrate unauthorised access to specific resources. The assessment will determine if the application is vulnerable to vulnerabilities (these vulnerabilities would be based on OWASP top 10 applications such as:
The primary purpose of this testing is to identify and exploit application and/or code vulnerabilities to demonstrate unauthorised access to specific resources. The assessment will determine if the application is vulnerable to vulnerabilities (these vulnerabilities would be based on OWASP top 10 applications such as:
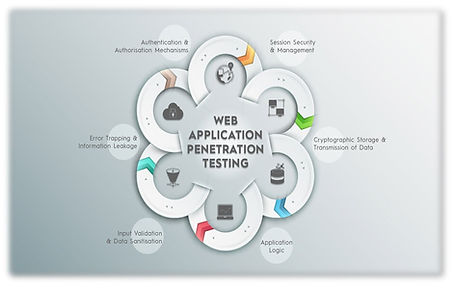

Methodology and approach (cont.)
Mobile Application Penetration Test
The mobile application testing service consists of a controlled security review against mobile application that run on mobile platform i.e. iOS or Android. The primary purpose of this testing is to identify and exploit application and/or code vulnerabilities to demonstrate unauthorised access to specific resources. The assessment will determine if the mobile application is vulnerable to vulnerabilities (these vulnerabilities would be based on OWASP top 10 mobile security risks such as:
Methodology and approach
Network Penetration Test
A penetration test, also known as a pen test, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. In the context of web application security, penetration testing is commonly used to augment a web application firewall (WAF).



OUR TEAM

Pavaris Jintanapramoth
•2 Year in Large Bank, Role: Head of App Pentest & Redteam (VP)
•1 Year in Large Healthcare, Role: Ex-Head of IT Security
•1 Years in Large Bank, Role: Ex-KBTG Lead Penetration tester
•6 Years in Big Four Firm, Role: Ex-Deloitte Cyber Security
•4 Years in Local Firm, Role: Cyber Security Consultant





